A NEW BREED OF AI FOR UNPARALLELED THREAT DETECTION
Manage cyber risk across your entire infrastructure
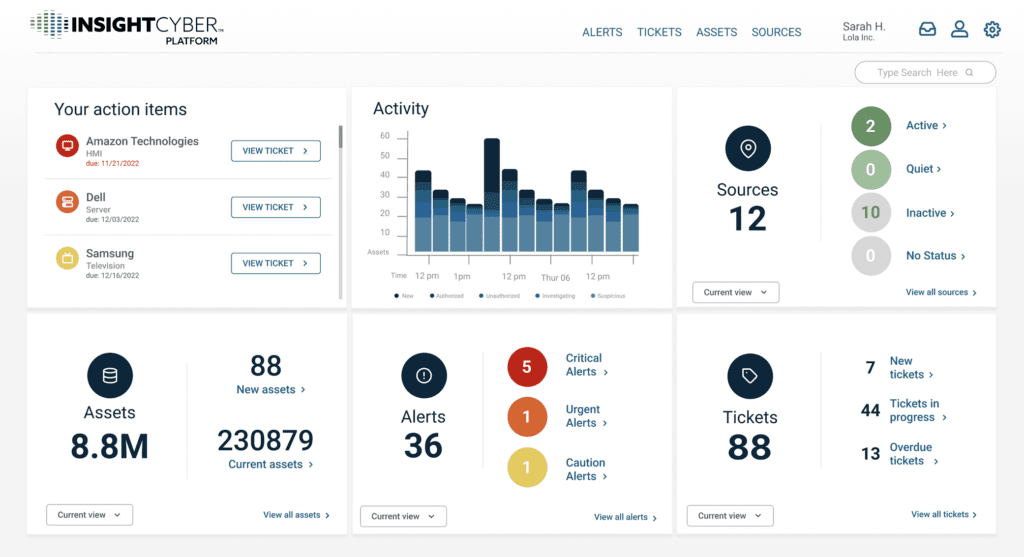
From the latest OT exploits to AI-driven identity compromises, InsightCyber’s Genomic AI delivers real-time detection against threats of any kind, in any asset or environment.
Go Deeper, Detect Faster with Genomic AI
Powerful Detection with Limitless Coverage
Analyzes any time-series data to detect and prioritize critical threats in real time — resulting in far fewer false alerts.
Quick Value, Minimal Effort
Instantly builds a full asset inventory and delivers rich alerts with risk levels, root causes, and recommendations — no endless scripting required.
Simple Deployment and Integration
Drop in a low-touch sensor, let it self-learn, and stream alerts into your stack — value delivered with near-zero overhead.
What LLMs do for language, Genomic AI does for processes
InsightCyber’s Genomic AI builds precise behavioral baselines for any environment faster than any other solution.
It filters out irrelevant data before it reaches your SIEM, cutting storage costs, lowering processing demands, and helping your SOC team focus on what truly matters.
AI or not – results matter
Every vendor tells a story of AI superpowers. And we know testing new tech is costly — so we’ve made it as easy as possible.
Request access to experience the power of Genomic AI free for 3 months, no strings attached.
InsightCyber values your privacy. We will protect your personal information and will not sell it to any third parties. You can opt-out any time. Read our Privacy Policy.
